WhatsApp voice message phishing emails push info-stealing malware
[ad_1]

A new WhatsApp phishing marketing campaign impersonating WhatsApp’s voice message attribute has been identified, trying to spread details-thieving malware to at minimum 27,655 e-mail addresses.
This phishing marketing campaign aims to direct the receiver by way of a series of techniques that will ultimately finish with the set up of an facts-stealing malware an infection, opening the way to credential theft.
Facts-stealing malware is aggressively distributed currently by using many usually means, with phishing remaining a main channel for risk actors.
The details stolen by these exclusive-purpose malware equipment is predominately account qualifications saved in browsers and applications but also targets cryptocurrency wallets, SSH keys, and even information saved on the computer.
WhatsApp voice messages as a entice
The new WhatsApp voice concept phishing campaign was learned by scientists at Armoblox, who are constantly on the lookout for new phishing threats.
For decades, WhatsApp has had the means to send voice messages to consumers in groups and non-public chats, with the characteristic obtaining new enhancements last week.
A well timed phishing attack pretends to be a notification from WhatsApp stating that they acquired a new non-public concept. This e mail functions an embedded “Play” button and audio clip period and creation time specifics.
The sender, masquerading as a “Whatsapp Notifier” support, is using an email address belonging to the Centre for Highway Safety of the Moscow Region.
.jpg)
Because of to this getting a legitimate and genuine entity, the messages are not flagged or blocked by e mail safety solutions, which commonly is the biggest challenge for phishing actors.
Armoblox believes this is a case of the hackers owning somehow exploited the domain to boost their purpose, so the organization plays a purpose without knowledge.
If the receiver clicks on the “Engage in” button in the information body, they are redirected to a web site that serves an permit/block prompt for installing a JS/Kryptic trojan.
To trick the target into clicking on “Permit,” the threat actors show a world-wide-web web page stating that you require to simply click ‘Allow’ to validate you are not a robot. However, clicking these allow buttons will subscribe the user to browser notifications that mail in-browser commercials for frauds, adult sites, and malware.
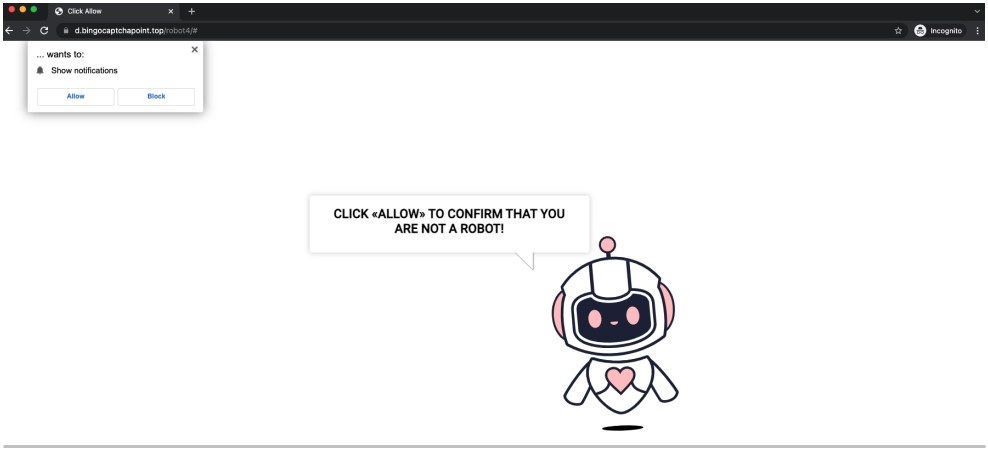
This very simple trick can be pretty powerful with people today who are not consciously aware or considering two times about their actions on-line.
Once the “allow” alternative is pressed, the browser will prompt the consumer to install the payload, which in this situation is an details-thieving malware.
How to safeguard by yourself
The truth that the emails in this campaign bypassed various secure electronic mail solutions tends to make it a notably awful case, but the clues that it was phishing have been continue to considerable.
First, the electronic mail handle has very little to do with WhatsApp, and the similar goes for the landing URL that requests the victims to simply click “Allow” to verify they’re true. They are both equally obviously out of WhatsApp’s area room.
Secondly, voice messages gained on WhatsApp are downloaded routinely in the consumer app, so the IM company would under no circumstances advise you about getting just one through electronic mail.
Thirdly, the phishing electronic mail options no WhatsApp brand, which is nearly certainly to avoid having issues with the VMC checks released by Gmail previous yr.
To safeguard by yourself from phishing attempts, often take your time to search into opportunity indicators of fraud when getting messages that make shocking promises, and by no means soar into motion.
If you require to look at a little something, do it on your own through the official website or application, and hardly ever by pursuing URLs or directions offered in the information.
[ad_2]
Resource hyperlink
